You can use Password Cruncher to recover a lost password for an encrypted volume that you've previously created with TrueCrypt or VeraCrypt.
This software uses the brute force method to recover the password. That is, you specify the character sets you want to try (lower-case, upper-case, digits, etc.) as well as the minimum and maximum length of the passwords, and Password Cruncher tries each character combination until it comes across the one that unlocks the encrypted volume:
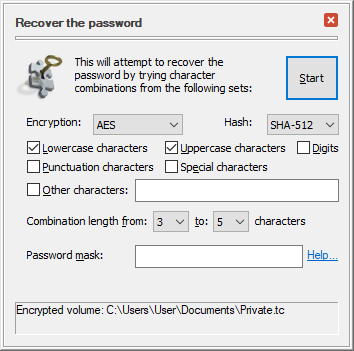
At this time the software can only recover the passwords to the file-based volumes encrypted with TrueCrypt or VeraCrypt software using the following algorithms:
What is NOT SUPPORTED at this time:
Basically, it means that Password Cruncher should be able to recover a lost password to a file-based volume encrypted with VeraCrypt or TrueCrypt (v.6.0 or later), unless a key file, a PIM, or one of the exotic or combination ciphers was used.
No, sorry. We may add such capabilities in the future, though, if we see enough interest in this software.
More information:
• Copyright ©2025 WinAbility Software Corp. All rights reserved. • Legal notices • Privacy policy •